
Photo by Markus Spiske on Unsplash
Unraveling the Mysteries of Cryptography: Safeguarding Secrets in the Digital Age(part-1)
Cryptography as the Cornerstone of Cybersecurity
1. A Brief History of Cryptography:
- Ancient Origins:
- Egypt and Greece: Cryptography finds its roots in ancient civilizations like Egypt and Greece. In Egypt, hieroglyphs served as a form of writing, possibly concealing meanings known only to a select few. In Greece, the Spartan military employed a form of cryptography known as the Scytale, where a message written on a strip of parchment wrapped around a cylinder could only be deciphered with a cylinder of the same diameter.
- Medieval Innovations:
Substitution Ciphers: During the Middle Ages, encryption methods became more sophisticated. One notable innovation was the substitution cipher, where each letter in the plaintext is replaced by another letter according to a fixed system. An example is the Caesar cipher, attributed to Julius Caesar, where each letter in the plaintext is shifted a certain number of places down the alphabet.
The Vigenère Cipher: Developed in the 16th century by Blaise de Vigenère, this cipher improved upon the Caesar cipher by using a keyword to determine the amount of shift applied to each letter. This made the encryption more secure, as the same letter in the plaintext could be encrypted differently depending on its position and the keyword.
- Modern Advancements:
The Telegraph and Radio: The 19th and 20th centuries saw significant advancements in communication technology, such as the telegraph and radio. These innovations created a need for secure communication over long distances, leading to the development of more sophisticated encryption devices.
The Enigma Machine: Perhaps the most famous encryption device of the 20th century, the Enigma machine was used by the German military during World War II to encrypt communications. It employed a series of rotors to scramble plaintext messages into ciphertext, making it extremely difficult for Allied cryptanalysts to decipher intercepted messages. The efforts of codebreakers like Alan Turing at Bletchley Park were instrumental in cracking the Enigma code, a breakthrough that significantly contributed to the Allied victory in the war.
Public-Key Cryptography: In the 1970s, public-key cryptography revolutionized the field of cryptography. Developed independently by Whitfield Diffie and Martin Hellman, and later by Ralph Merkle, public-key cryptography introduced the concept of asymmetric encryption, where separate keys are used for encryption and decryption. This innovation paved the way for secure digital communication and laid the foundation for modern cryptographic protocols such as SSL/TLS and PGP.
Conclusion:
The history of cryptography is a testament to humanity's ongoing quest to protect sensitive information from prying eyes. From ancient techniques like the Scytale to modern innovations like public-key cryptography, cryptographic methods have evolved in response to the changing landscape of communication technology and the ever-present need for secure communication. Today, cryptography plays a crucial role in ensuring the confidentiality, integrity, and authenticity of data in the digital age.
2. Fundamental Principles of Cryptography:
Confidentiality:
Confidentiality is a fundamental principle of cryptography that ensures sensitive information remains protected from unauthorized access. It involves encrypting data in such a way that only authorized parties can access and understand it, while unauthorized individuals or entities are unable to decipher the encrypted content.
Encryption Techniques: Cryptographic algorithms such as symmetric-key encryption (e.g., AES) and asymmetric encryption (e.g., RSA) are commonly used to achieve confidentiality. These algorithms scramble plaintext data into ciphertext using keys, making it unintelligible to anyone without the corresponding decryption key.
Application: Confidentiality is essential in various scenarios, including secure communication over networks, protecting sensitive personal information, securing financial transactions, and safeguarding classified government data.
Integrity:
Integrity ensures that encrypted data remains unchanged and unaltered during transmission or storage. It verifies that the information has not been tampered with or modified by unauthorized parties, maintaining its accuracy and reliability.
Hash Functions: Cryptographic hash functions, such as SHA-256 and MD5, play a crucial role in ensuring integrity. These functions generate a fixed-size hash value or checksum for a given input data, which acts as a unique digital fingerprint. Any alteration to the input data will result in a different hash value, indicating potential tampering.
Digital Signatures: Digital signatures are another mechanism used to ensure integrity. They involve applying a cryptographic algorithm to a message or document using the sender's private key, creating a unique signature. The recipient can verify the signature using the sender's public key, confirming the integrity and authenticity of the message.
Application: Integrity is vital in contexts such as electronic transactions, data storage, software distribution, and communication protocols, where ensuring the trustworthiness and reliability of data is paramount.
Authentication:
Authentication is the process of confirming the identity of senders and recipients of encrypted messages or data. It verifies that the parties involved are who they claim to be, establishing trust and ensuring the security of communication channels.
Digital Certificates: Authentication often relies on digital certificates issued by trusted Certificate Authorities (CAs). These certificates contain information about an entity's identity and public key, allowing recipients to verify the authenticity of their communication partners.
Challenge-Response Protocols: Some authentication mechanisms involve challenge-response protocols, where one party challenges the other to prove their identity by providing a specific response or authentication token.
Application: Authentication is critical in scenarios such as accessing secure systems, logging into online accounts, establishing secure connections in network communication, and verifying the authenticity of digital documents.
Non-repudiation:
Non-repudiation is a cryptographic principle that prevents individuals from denying their involvement in sending or receiving encrypted messages or transactions. It provides irrefutable evidence of the origin and receipt of data, ensuring accountability and preventing disputes or repudiation of actions.
Digital Signatures: Digital signatures play a central role in achieving non-repudiation. By associating a unique cryptographic signature with each message or transaction, individuals cannot deny their participation or disown their actions, as their signature serves as incontrovertible proof.
Audit Trails: Maintaining comprehensive audit trails of cryptographic operations and transactions can also contribute to non-repudiation by recording all relevant information, including timestamps, identities of involved parties, and cryptographic signatures.
Application: Non-repudiation is essential in legal and regulatory contexts, electronic commerce, financial transactions, contracts, and any scenario where accountability and proof of participation are required.
Conclusion:
The fundamental principles of cryptography - confidentiality, integrity, authentication, and non-repudiation - form the bedrock of secure communication and data protection in the digital age. By leveraging cryptographic techniques and algorithms, organizations and individuals can safeguard sensitive information, maintain trust in communication channels, and mitigate risks associated with unauthorized access, tampering, or denial of involvement. These principles underpin the design and implementation of secure systems, protocols, and applications, ensuring the confidentiality, integrity, and authenticity of data in an increasingly interconnected and digitized world.
3. Types of Cryptographic Techniques:
- Symmetric Cryptography:
Symmetric cryptography, also known as secret-key cryptography, involves using the same key for both encryption and decryption of data. This key is shared between the communicating parties and must remain secret to ensure the security of the encrypted communication. Symmetric encryption algorithms are generally faster and more efficient than asymmetric algorithms, making them suitable for encrypting large volumes of data.
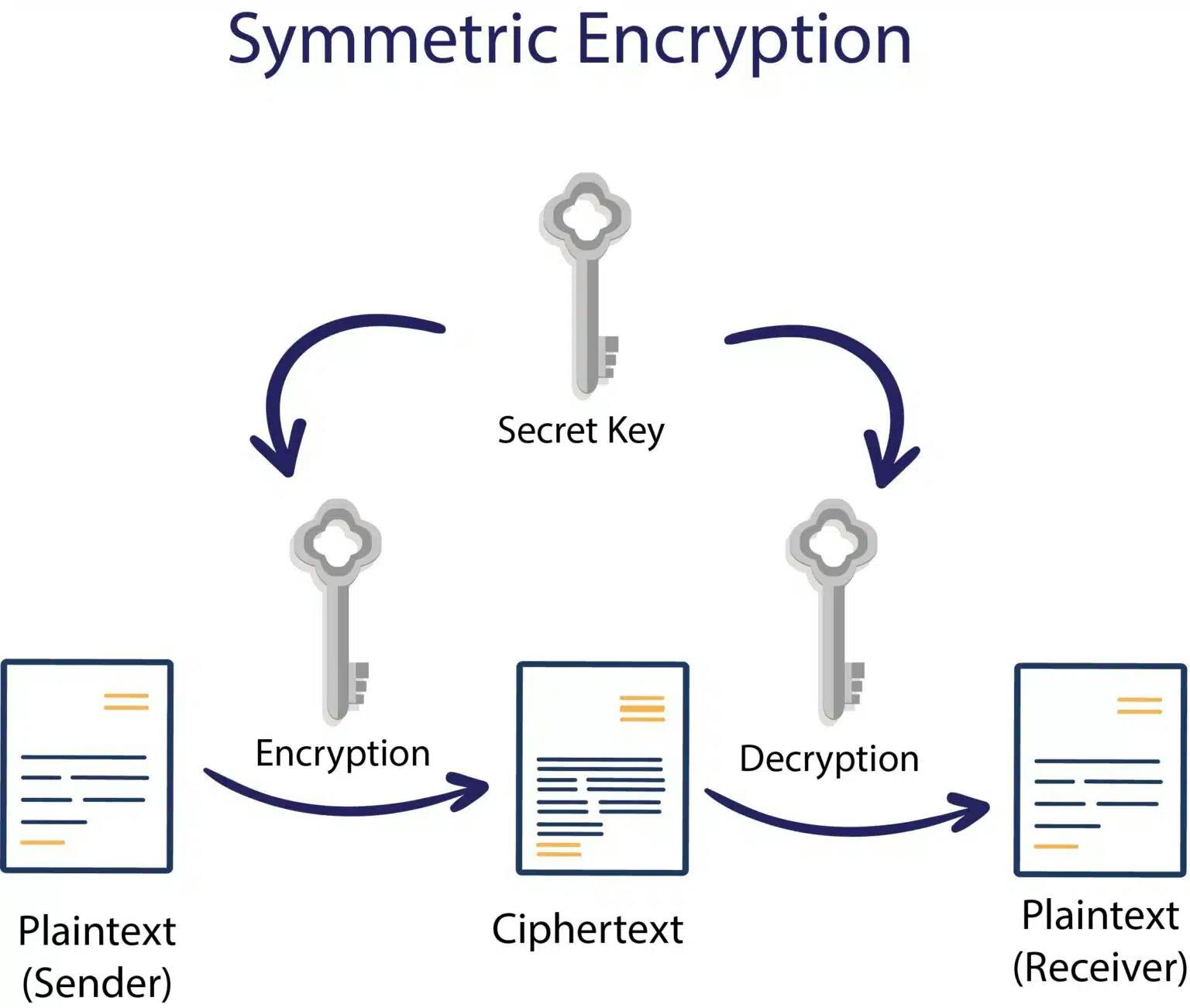
Key Characteristics:
Single Key: Symmetric cryptography employs a single secret key that is used for both encryption and decryption operations. This key is shared between the sender and receiver, ensuring that they can encrypt and decrypt messages securely.
Efficiency: Symmetric encryption algorithms are computationally efficient, making them well-suited for encrypting large amounts of data in real-time. They require less computational resources compared to asymmetric encryption, making them ideal for applications where performance is critical.
Examples: Classic symmetric encryption techniques include the Caesar cipher, where each letter in the plaintext is shifted by a fixed number of positions in the alphabet. Modern symmetric encryption algorithms include Advanced Encryption Standard (AES), which is widely used for securing data in various applications, including financial transactions, communication protocols, and data storage.
- Asymmetric Cryptography:
Asymmetric cryptography, also known as public-key cryptography, utilizes a pair of keys: a public key and a private key. These keys are mathematically related, but it is computationally infeasible to derive the private key from the public key. The public key is freely distributed and used for encryption, while the private key is kept secret and used for decryption.
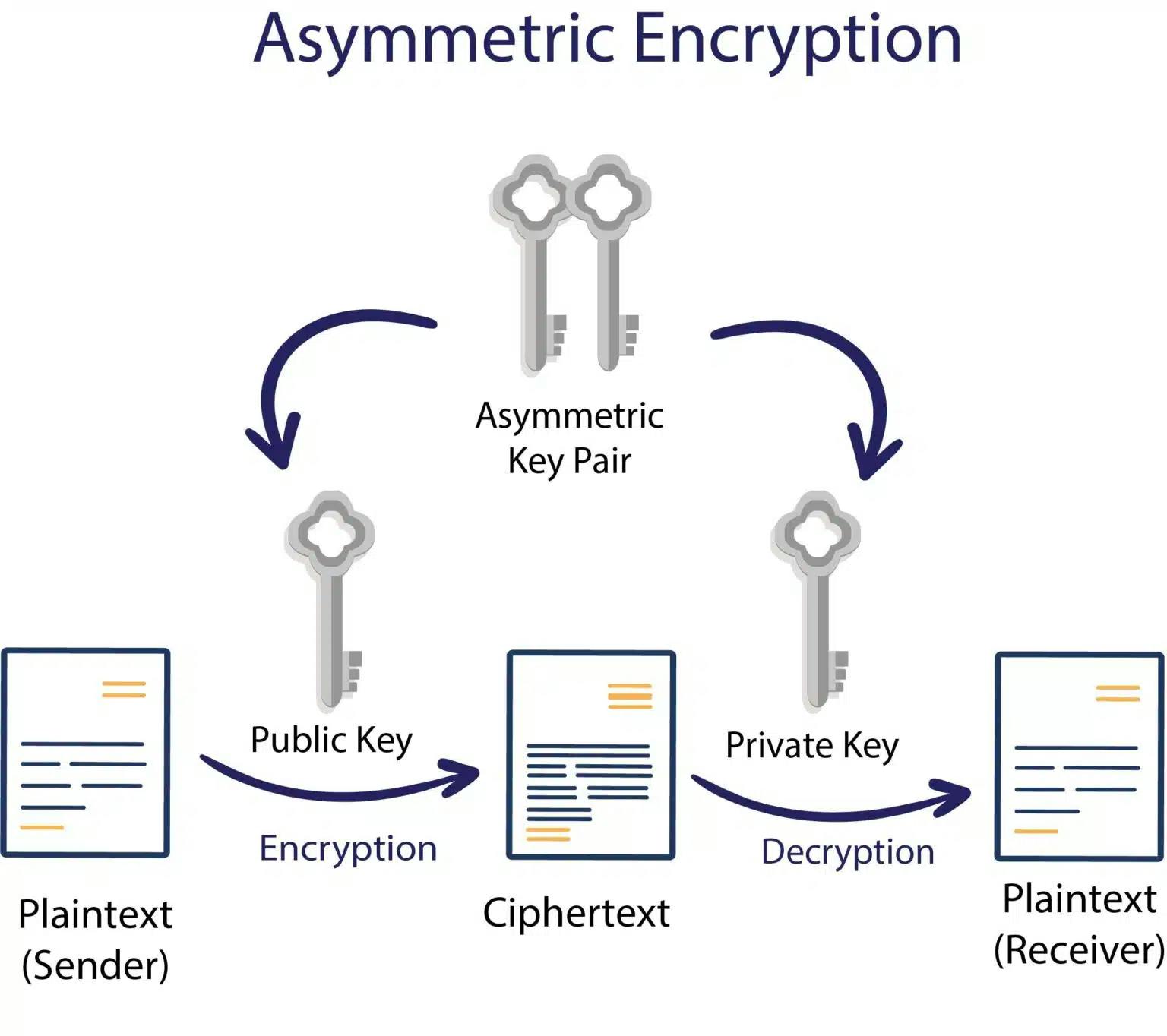
Key Characteristics:
Public and Private Keys: Asymmetric encryption employs two distinct keys: a public key and a private key. The public key is shared with anyone who wishes to send encrypted messages to the owner of the key, while the private key is kept secret and known only to the key owner.
Encryption and Decryption: Data encrypted with the public key can only be decrypted with the corresponding private key, and vice versa. This asymmetric relationship enables secure communication between parties without the need to share a secret key.
Examples: The RSA algorithm, named after its inventors Rivest, Shamir, and Adleman, is one of the most widely used asymmetric encryption techniques. It relies on the mathematical properties of large prime numbers to generate public and private key pairs. RSA is used in various applications, including secure email communication, digital signatures, and SSL/TLS encryption for web traffic.
Comparison:
Security: Asymmetric cryptography offers higher security compared to symmetric cryptography, as it eliminates the need to share secret keys between communicating parties.
Performance: Symmetric cryptography is faster and more efficient than asymmetric cryptography, making it preferable for encrypting large volumes of data.
Use Cases: Symmetric cryptography is suitable for applications where speed and efficiency are critical, while asymmetric cryptography is preferred for secure communication over untrusted channels and scenarios requiring secure key exchange.
Conclusion:
Symmetric and asymmetric cryptography are essential components of modern cryptographic systems, each with its unique strengths and applications. While symmetric cryptography excels in speed and efficiency, asymmetric cryptography provides enhanced security and facilitates secure communication over untrusted channels. Understanding the differences between these two cryptographic approaches is crucial for designing secure systems and selecting appropriate encryption techniques based on specific requirements and use cases.
Summary:
The history of cryptography spans ancient civilizations to modern innovations like quantum-resistant encryption. Fundamental principles ensure confidentiality, integrity, authentication, and non-repudiation. Symmetric and asymmetric cryptography offer different strengths, while real-world applications secure communication, data protection, e-commerce, and blockchain. Challenges include quantum computing and post-quantum cryptography, with emerging trends like homomorphic encryption and secure multi-party computation addressing future needs.
